I will summarise the changes (taken straight from Laszlo's site with no change here):
"The 0.22 has some speed advancement because of the prehash implementation and has some usefull changes:It is strongly recommended to use this new release. The list of some repaired bugs can be found here (thanks Michael Donnerer for reporting them). This is still an early release, so it needs massive bug hunting and code cleaning."
- Prehash implementation in the brute-force mode of the password hash.
- Prehash implementation in the dicitonary mode of the password hash (if the username len > 4)
- It saves the list of the index of the found passwords, so you can use --prev paramter to leave out the already cracked passwords from a previous session. In the session continue mode (-s), it loads the results automaticly.
- The order in the permutation engine was changed to follow a more logical way (thanks for Pete Finnigan suggesting it).
- The permutation engine has more parameters that controls which permutation should be included.
This is a worthwhile release to download and use at least for the speed increases. I have used Laszlo's cracker for quite some time now on professional database audits and always found it a useful tool.
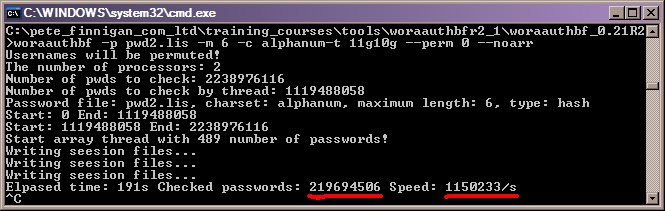
I just did some simple tests comparing version 2.1 and version 2.2 of Laszlo's cracker. The first picture shows version 2.1 running for a single password using brute force. I ran the cracker for around 3 minutes to let it speed up and show a reasonable average:
I then ran the new woraauthbf cracker, version 2.2 and did exactly the same test:
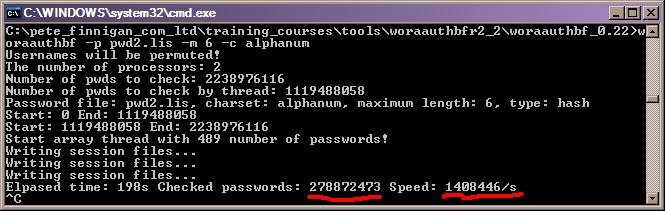
The results are as expected and much faster than the earlier version. We see an increase in speed from 1.15 Million hashes a second to 1.4 million hashes a second. This is a 22.45% speed increase on my laptop. Quite impressive Laszlo!
The speed increase will not be as impressive for dictionary attacks as the word order cannot be guarenteed in a dictionary file to take full effect of the pre-hashing implemented by Laszlo.

















