I first chatted to Dennis Yurichev probably around a couple of years ago about his efforts to make an FPGA password cracker. We exchanged numerous emails and i think without checking back he had one FPGA cracker working that did 76 million hashes per second. Well Dennis has finally finished up his cracker and has added a web based front end to the hardware that is accessible from his website. Dennis emailed me this morning to test it out but when i tried unluckilly he had a power outage. Now his site is back up and you can go there and submit Oracle usernames and password hashes to be queued to run on the hardware. I submitted a user "DY" with a password of GH56BG8
SQL*Plus: Release 11.1.0.7.0 - Production on Mon Oct 5 12:21:05 2009
Copyright (c) 1982, 2008, Oracle. All rights reserved.
Connected to:
Personal Oracle Database 11g Release 11.1.0.7.0 - Production
With the Partitioning, OLAP, Data Mining and Real Application Testing options
SQL> create user dy identified by gh56bg8;
User created.
SQL> select name,password from sys.user$
2 where name='DY';
NAME PASSWORD
------------------------------ ------------------------------
DY 4BD6926200326C0E
SQL>
|
The FPGA cracker is available at
Dennis's site, simply cut and paste the username and the hash into the boxes on the screen, Dennis queues the job to run on the cracker. The screen updates to give you progress.
Here is a look at the cracker running (click the image to increase it):
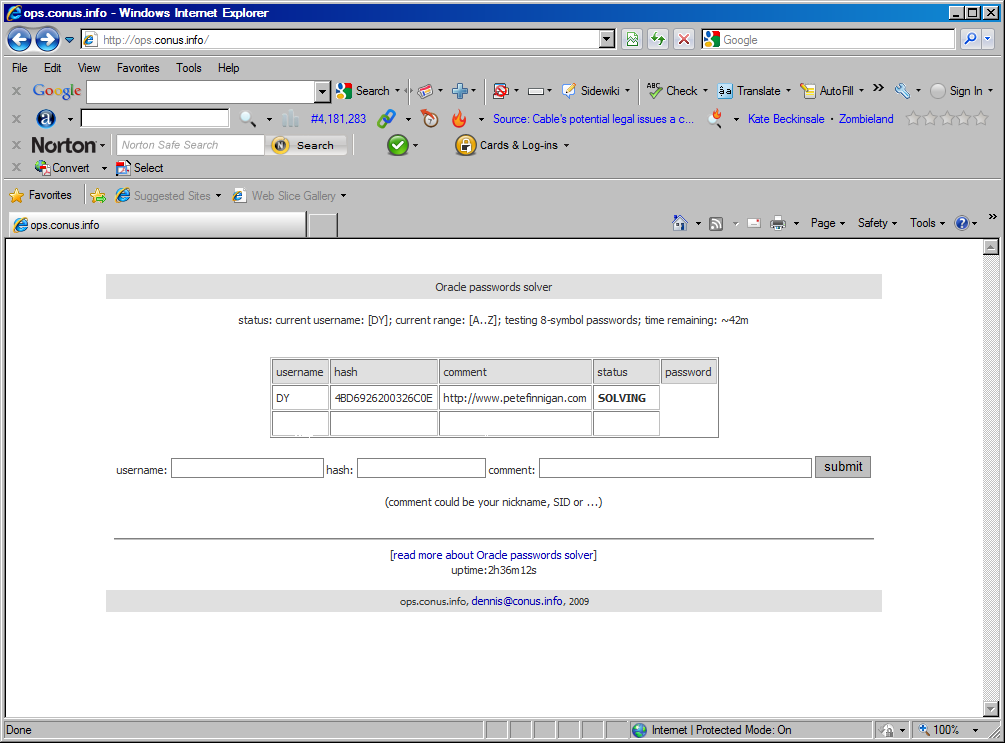
The
Oracle RDBMS passwords solver page gives some details, make sure that you don't post production passwords/hashes as these will be displayed publically.
Nice site Dennis, it will be interesting to see how much it gets used.



















October 5th, 2009 at 01:40 pm
Pete Finnigan says:
Needless to say, it is currently working only in A-Z passwords range, for the sake of demonstration speed. Full A-Z0-9#$_ range will demand 16.5 hours.