The last few weeks have been very busy with full time client work and also a number of personal projects so emails and blogging have taken a back step. Coupled to that I have used my writing time with a different focus than the website and blogging which is in one sense a pity but on the other hand its nice to actually produce some content that will be printed.
So for the last few weeks i have used up spare time first writing the first article for the Oracle Scene Magazine on Oracle security which hopefully will become a regular column.
Mark Rittman is now the editor for http://www.ukoug.org/publications/index.jsp?parent=0&id=1 - (broken link) Oracle Scene magazine and he asked me some time ago if I could write something, so I was happy to do so. My first article is on powerful privileges.
Next I spent a lot of spare time over the last month or so writing two chapters for the new Oak Table Book: tentitively titled
"Expert Practices: Oracle database administration from the Oak table". This is hard when working all day and quite often travelling to spend evenings also writing. The two chapters I have written "Securing Users" and "Securing Data" are now draft.
I have also been working to get our new product
PFCLSCan progressed. The development of the back end engine is complete and the development of the console GUI is coming on well and i though a couple of pictures would be in order to show you what it looks like. Here is a look at the front end:
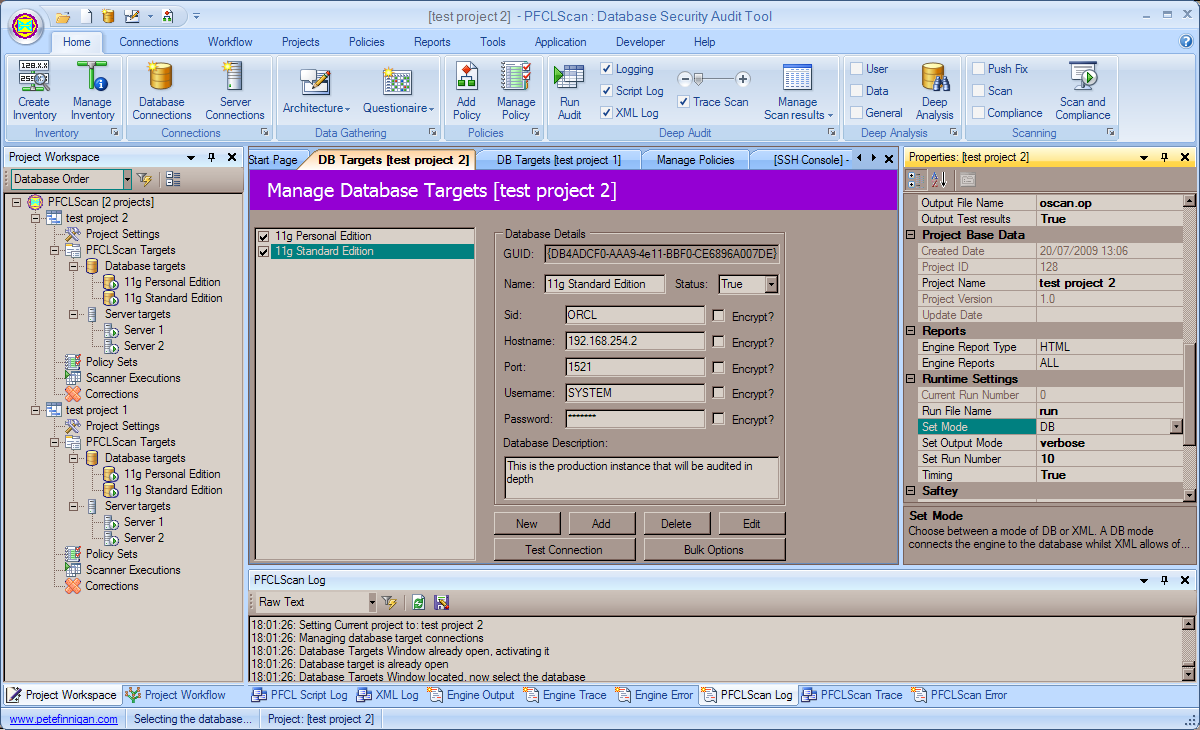
Note: Click on the link to increase the picture size
This picture shows the main GUI console structure. The main screen in the middle is the screen to manage database connections. The tree view to the left is the project workspace that allows you to manage as many projects as you wish to have open at the same time. The right hand properties window allows you to manage the settings for the current project (This is indicated in the title bar). The settings are used by the back end engine and also the GUI. The windows at the bottom of the screen allow viewing/clearing/filtering and saving of logs/ trace / errors generated by the engine and also the console. The engine also has a built in script engine with our own scripting language called PFCLScript. The logs from the script compiler/interpreter can also be viewed as well as logs from the uiltin XML parser. Thats a brief look at what the console looks like. Another view is of the tools Window:
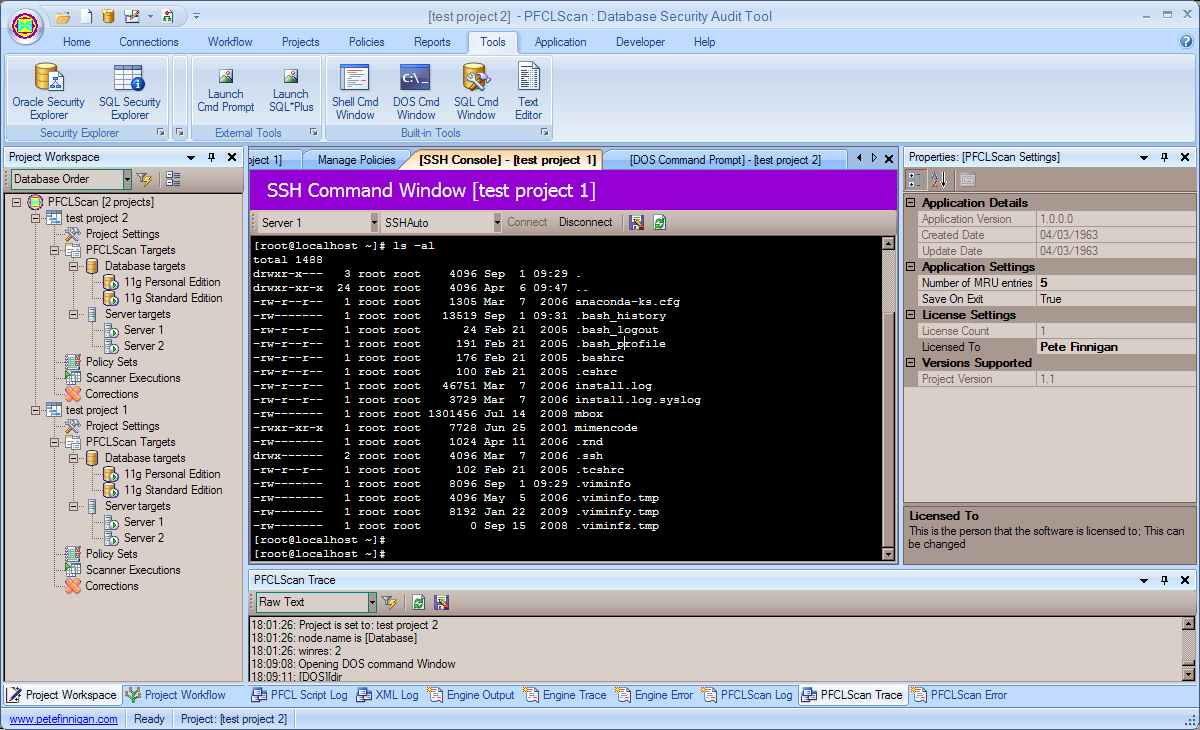
Note: Click on the link to increase the picture size
The tools window allows access to the builtin shell command window (shown in the picture). Whilst the whole tool is project based and within projects the tests are based on checks that are XML based (we allow a lot of different types of checks, SQL, PL/SQL, Shell script, external tools, builtin tools (e.g. password cracker), PFCLScript, questionaire, architecture and more... we also support complex type checks that can be modified at compile time, at run time and we also support loop checks. All of these complex checks can be applied to any of the previous types of checks. This makes complex audit easy to do and configure. Whilst we do all of this and a lot lot more that I will talk about and show you next time we also have access to a number of built in and external tools. At the simplest level there is a complete built in shell for accessing Unix servers either using ssh or telnet and also ssh1 and ssh2. The picture above shows the shell command Window in use.
We also have a built in SQL tool that allows the running of SQL or PL/SQL scripts. We also have a completely builtin DOS (NT cmd) box that allows any command to be run on the server hosting the GUI. These are all tied to the current project so that ad hoc checks and investigations can be completed and also attached to the project in the same format as all other output (XML). Each of these tool windows support saving to file (raw text or XML) and also clearing. We also have access to external tools such as SQL*Plus and also a GUI SQL explorer type Window.
I hope thats a nice taste of whats to come. Watch out, I will talk in a lot more detail over the coming weeks about more of PFCLScans features.
Finally, Dirk Nachbar emailed me to let mw know of a bug in Oracle reports that I talked about here in a post titled "
A nice fix for the "Overwrite any file via desname in Oracle Reports" bug". Dirk has let me know that Oracle has finally fixed this/ worked around it in Oracle reports 11g. Dirk has mentioned some details in his own blog in a post titled "
Oracle reports desname bug fixed with Fusion Middleware 11g". Dirk also let me know of another security bug he has found in the Fusion middleware WebLogic server. The administrator user and password are displayed in clear text in a
ps listing. Again Dirk has talked about this in his blog, this time in a post titled "
Security hole in Fusion middleware 11g weblogic admin server".






















