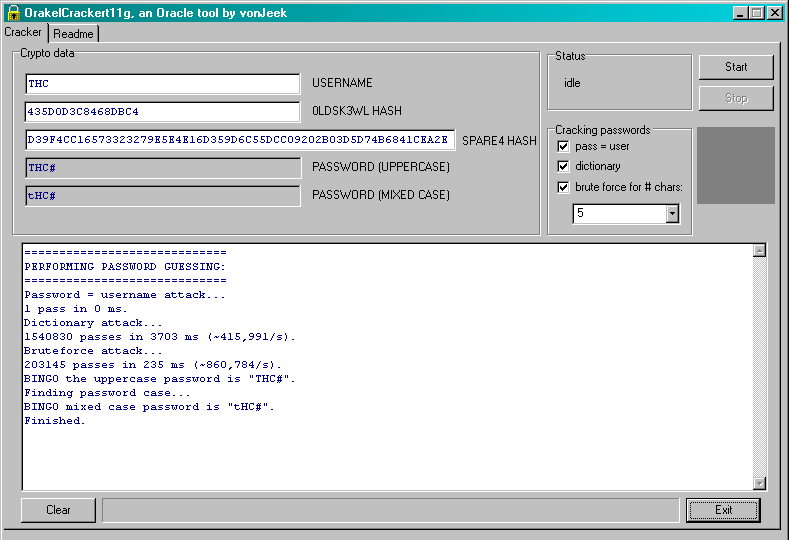
The password cracker exploits the fact that the old DES hash is stored. Therefore the upper case version of a password can be cracked first. If the password guessed generates a hash that matches that stored in the SYS.USER$.PASSWORD column then a further attack can be made on the SHA-1 hash to determine the case sensitive version of the password. This reduces the number of guesses necessary. As you can see the tool is graphically based and does a test based on user=pwd, dictionary attack then a brute force attack using the old DES based hash first. The readme is shown below:
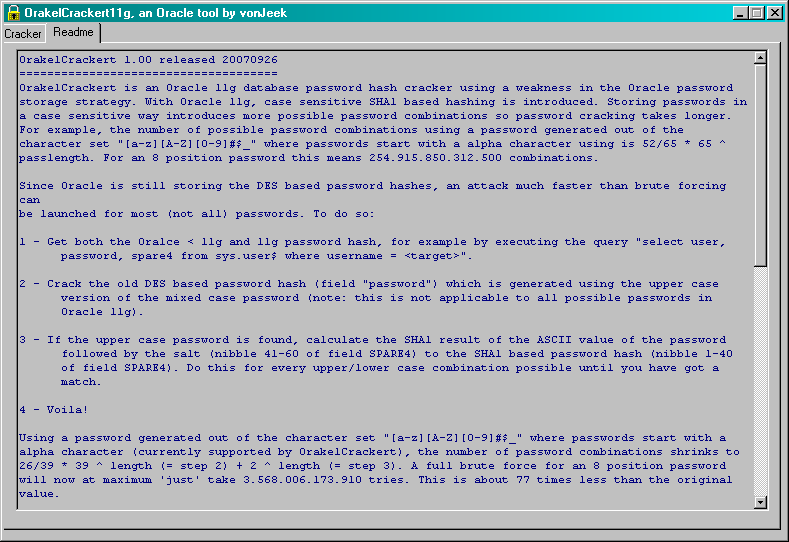
explains how the cracker works. Nice tool!!




















