- Oracle password hash attack
- Oracle password hash attack for 11g. It tries to crack the old hash and checks the case sensitivity with the new algorithm.
- 8i authentication attack without oracle dlls
- 9i and 10g authentication attack with oracle dlls
- Dictionary attack
- Incremental brute force attack
- Multithreaded
- Resume mode
Laszlo's tool also does an Oracle 8i, 9i and 10g authentication attacks as shown in his paper talked about here yesterday.
I did a couple of quick tests to see how woraauthbf works with an Oracle 11g password. First i used a simple peice of SQL from Laszlo's paper to get the details in 11g for the SCOTT user to crack his password:
SQL> select u.name||':'||u.password||':'||substr(u.spare4,3,63)||':'||d.name||':'||sys_context('USER 2 from sys.user$ u, sys.V_$DATABASE d where u.type#=1 3 and u.name='SCOTT' 4 / U.NAME||':'||U.PASSWORD||':'||SUBSTR(U.SPARE4,3,63)||':'||D.NAME||':'||SYS_CONTE -------------------------------------------------------------------------------- SCOTT:F894844C34402B67:CC92BE1125BD6136A74370F64B3957C9016402C0214E307BFCD34EF02 806 |
Then i saved this to a file called 11g_test.txt:
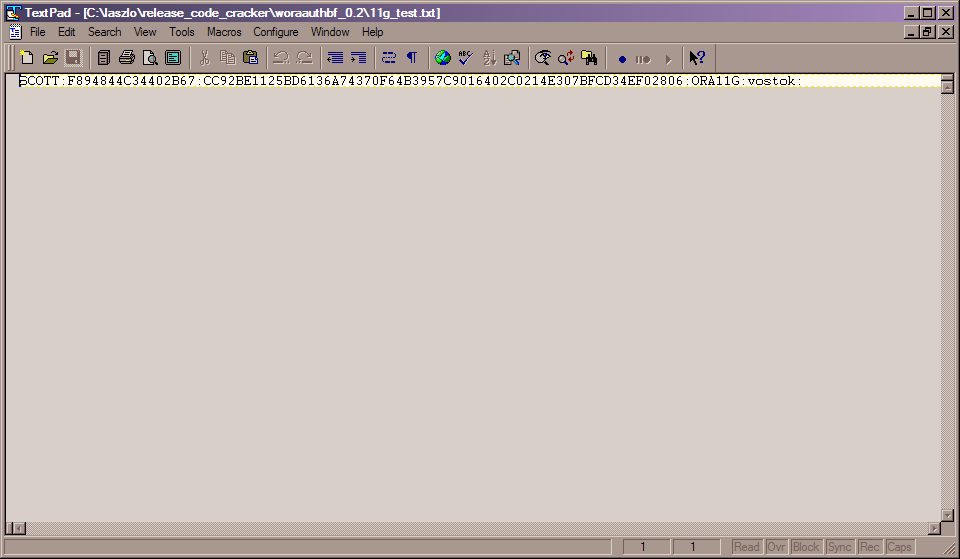
The text file is called 11g_test.txt and is available from here. OK, now I can run the password cracker. I first run in dictionary mode and I used Alex Kornbrusts excellent password_file.txt included with his checkpwd tool. Here is the output:
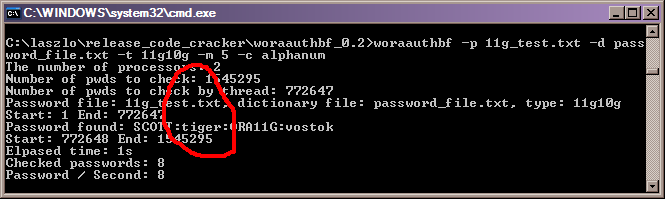
That clearly shows that the cracker performed well and found that SCOTT still has its default password of TIGER except that its in lower case, it correctly found that I had set the password to the lower case value but it also worked fast as tiger is still a default password irrespective of the case of the leters used. Next I changed the password for the SCOTT user in SQL*Plus, i first saved the SQL select statement that is used to get the details the cracker needs:
SQL> save pwd.sql Created file pwd.sql SQL> alter user scott identified by Cra3k; User altered. SQL> @pwd U.NAME||':'||U.PASSWORD||':'||SUBSTR(U.SPARE4,3,63)||':'||D.NAME||':'||SYS_CONTE -------------------------------------------------------------------------------- SCOTT:9B5981663723A979:71C46D7FD2AB8A607A93489E899C08FFDA75B147030761978E640EF57 C35 SQL> |
And then I saved the output to a new file called 11g_test2.txt with the same format as the first file. Then I could run the cracker againin dictionary mode:
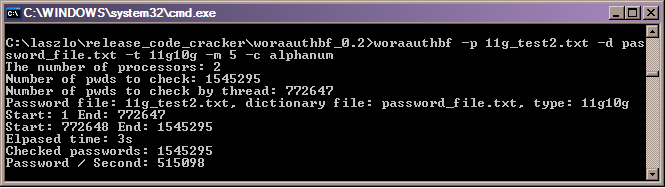
This time the password is not found (as its not a dictionary word - well not in this dictionary, if the orabf permute tool was used it would most likely have found it). The tool is very fast though in dictionary mode, it is going at 515,000 hashes per second on my dual core laptop and did the whole file in 3 seconds. Lets now run the cracker in brute force mode and see if it can find the password (I used the same file 11g_test2.txt):
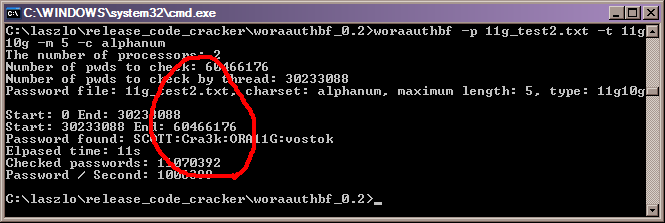
This tool is fast, over one million hashes per second (faster than orabf on the same machine) and faster in terms of elapsed time also and of course it found the case sensitive password.


















October 9th, 2007 at 11:22 am
Pete Finnigan says:

While its brute force speed is impressive, saying that it is the fastest oracle password cracker is misleading. Password cracking is not just about pwd/s, it is also about how you choose these passwords.
Based on my observations on real passwords, John the Ripper (incremental mode) has the same discovery rate than a "stupid" brute forcer when the brute forcer runs 35 times faster, even when it orders letters by order of appearance instead of alphabetic order. (Based on a large pwdump output, about 7000 *french* accounts. This is not so scientific, and might only apply to french passwords ...)
And of course Markov filtering is lots better