Today I want to look at wallets at a most basic level and the password used to protect a wallet. Can we create weak passwords (NOTE: We don't WANT to do that; I just want to understand if we can)
First lets create a wallet on a 19c database installed server. First lets create a directory to put the wallet in:
[oracle@oel19cee ~]$ mkdir wallets
[oracle@oel19cee ~]$ cd wallets
[oracle@oel19cee wallets]$
First can we create a wallet without a password:
[oracle@oel19cee wallets]$ orapki wallet create -wallet .
Oracle PKI Tool Release 19.0.0.0.0 - Production
Version 19.3.0.0.0
Copyright (c) 2004, 2019, Oracle and/or its affiliates. All rights reserved.
Enter password:
Enter password again:
Operation is successfully completed.
[oracle@oel19cee wallets]$
Good, if I create a wallet and don't specify the password it asks me for one. What if I do the same and specify auto login:
[oracle@oel19cee wallets]$ rm ewal*
[oracle@oel19cee wallets]$ ls -al
total 4
drwxr-xr-x. 2 oracle oinstall 6 Feb 23 12:46 .
drwx------. 20 oracle oinstall 4096 Feb 23 12:43 ..
[oracle@oel19cee wallets]$ orapki wallet create -wallet . -auto_login
Oracle PKI Tool Release 19.0.0.0.0 - Production
Version 19.3.0.0.0
Copyright (c) 2004, 2019, Oracle and/or its affiliates. All rights reserved.
Enter password:
Enter password again:
Operation is successfully completed.
[oracle@oel19cee wallets]$
Good, again, we cannot create a wallet without a password. OK, so can we create a wallet with a weak password:
[oracle@oel19cee wallets]$ orapki wallet create -wallet . -auto_login -pwd a
Oracle PKI Tool Release 19.0.0.0.0 - Production
Version 19.3.0.0.0
Copyright (c) 2004, 2019, Oracle and/or its affiliates. All rights reserved.
PKI-01002: Invalid password. Passwords must have a minimum length of eight characters and contain alphabetic characters combined with numbers or special characters.
[oracle@oel19cee wallets]$
So, we tried to create a wallet password of a and orapki didn't let me. It states that the password must be at least 8 characters and have numbers OR special characters. This means that we are not forced to use alpha, numeric and specials as that would increase the number of possible passwords to hack. It also doesn't state that we have to use UPPER and LOWER again this weakens the possible passwords available as well. We don't know the number of possible special characters that can be used in a password but we know the digits is 10, 0-9 so lets assume there are more than ten specials so the possible character space is 36 possible characters so a-z0-9. Remember we dont have to use specials.
Lets try a simple password:
[oracle@oel19cee wallets]$ orapki wallet create -wallet . -auto_login -pwd 1111111a
Oracle PKI Tool Release 19.0.0.0.0 - Production
Version 19.3.0.0.0
Copyright (c) 2004, 2019, Oracle and/or its affiliates. All rights reserved.
Operation is successfully completed.
[oracle@oel19cee wallets]$
This weakens the password somewhat as we allow 10 possible passwords in the first 7 slots and 26 in the last one. So we would have [using ^ to mean to the power] = 10^1 + 10^2 + 10^3 + 10^4 + 10^5 + 10^6 + 10^7 + 36^1 - we assume in this example that one character is a-z and is in position 8 and positions 1 - 7 are digits 0-9. So we have 10 + 100 + 1000 + 10000 + 100000 + 1000000 + 1000000 + 36 = 11,111,146 which is 11.1 million possible passwords. If a password cracker is doing 200 million guesses per second that would last 0.05 seconds only if we know the password construction - i.e. places 1-7 are digits and the last place is a-z.
OK, that's an extreme example and not real. Lets assume that all 8 slots can be 0-9a-z so 36 possible characters. So repeat the calculation this time in Excel:
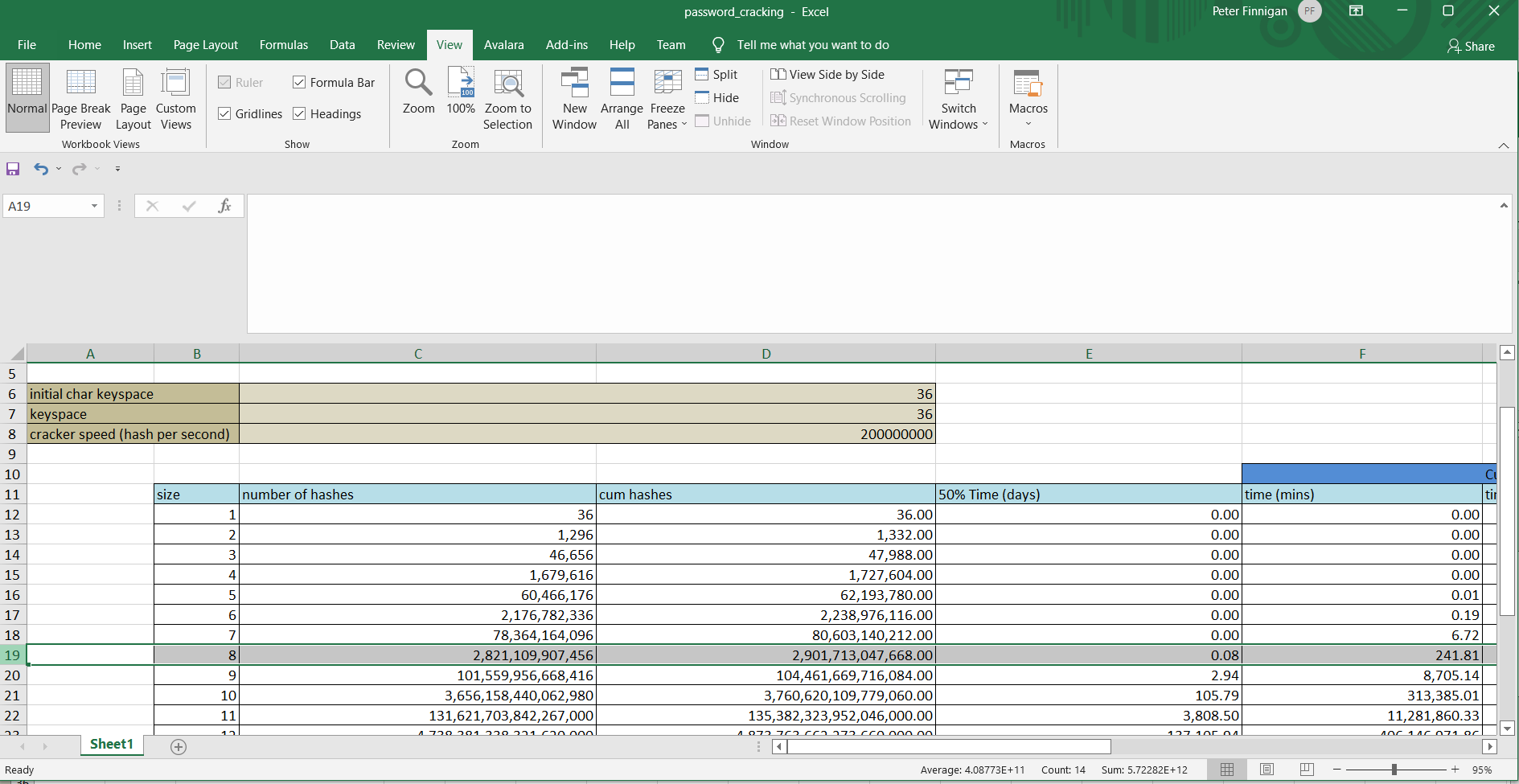
As we can see there are 2.9 trillion possible passwords and this would take around 4 hours on average to crack using a cracker running at 200 million guesses per second. This is a reasonable speed in this day and age as GPU based cracker because of bit coin mining can go enormously faster. This assumes that we can extract the password hash from the wallet and we know the algorithm used.
BUT there are no rules to force a user to only use lower case and digits (that's the minimum we can get away with) and a user can use upper case and specials. So we need to change the calculation to be a-zA-Z0-9#%$... so lets say 26+26+10+10 = 72 possible characters. The calculation is then:
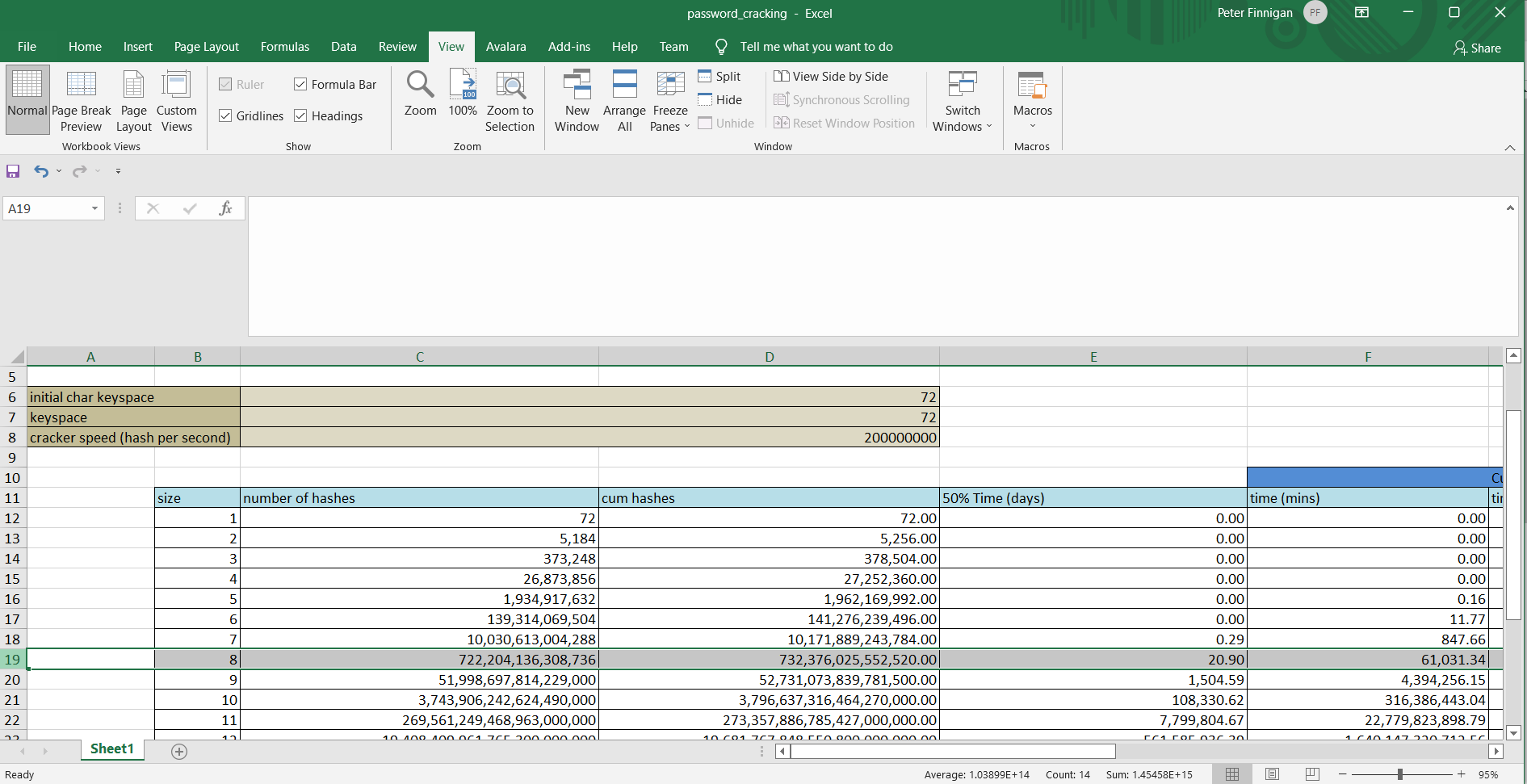
This is much better as it will now take 20.9 days to crack this password using the same cracker speed using the asumption that on average passwords will be cracked in 50% of the time needed to crack all possible combinations; some passwords might start with aaaaaa... and some zzzzzz... so because crackers start a,b,c... and then aa,ab,ac... and so on we would assume that some passwords are cracker faster than others so lets just use 50% of the time as an average or 42 days if we try all possible options.
We can simply create dictionary words:
[oracle@oel19cee wallets]$ orapki wallet create -wallet . -auto_login -pwd Passw0rd
Oracle PKI Tool Release 19.0.0.0.0 - Production
Version 19.3.0.0.0
Copyright (c) 2004, 2019, Oracle and/or its affiliates. All rights reserved.
Operation is successfully completed.
[oracle@oel19cee wallets]$
This makes cracking faster so instead of trying trillions of passwords we might try millions of words and "leet" speak.
There is no way to force upper, lower, digits and specials on wallets. People will gravitate to dictionary and lower and digits so the assumption would be that wallets can be cracked in hours or minutes if dictionary words are used. Make sure that when you create wallets for SSL, TDE etc that you use longer passwords than 8 characters and you use the full keyspace and do not include dictionary words.
Contact me at pete at petefinnigan dot com or DM me on social media if you would like any help with SSL and Oracle




















