Like most companies you probably want to protect your PL/SQL code in terms of protecting loss of IPR or knowledge of how you have created your logic and also in terms of protecting your application from someone running it when it is not supposed to be run. When you deploy an APEX application to a customers database you lose control of the code; it is in someone elses database therefore it makes sense to protect that code before it is deployed in terms of obfuscating it and also by adding license type features to control when its allowed to run.
Our product PFCLObfuscate can be used to protect PL/SQL applications. We also announced the ability to add license type features to your PL/SQL last year in a post titled "PFCLObfuscate - Protect your PL/SQL"
We were approached by someone a few months ago to ask if we could at that time protect PL/SQL APEX applications. We are not APEX experts (yet! - if ever!) so we had a look at a sample exported APEX application provided to us and thought.... "It's just a SQL*Plus script with a bunch of anonymous blocks" ..... PFCLObfuscate should work as we could obfuscate any PL/SQL code and also SQL*Plus scripts containing anonymous blocks.
That was a few months ago and after some testing and playing around at that time it sort of worked and sort of didn't. There were some APEX specifics to overcome and we left it for a while due to other development committments. Just recently we have been able to work on APEX support in PFCLObfuscate again and learn enough APEX to build our own simple applications to test with. Now we have a working version of PFCLObfuscate protecting APEX PL/SQL. All our existing customers will receive a download link to get the new version in the next week or so as we finalise the changes and update the manual but I wanted to show you today that PFCLObfuscate can protect Oracle APEX Applications.
We have created a simple application - it is really simple - but good enough as a test bed to show obfuscation and protection works. Here is a view of the application:
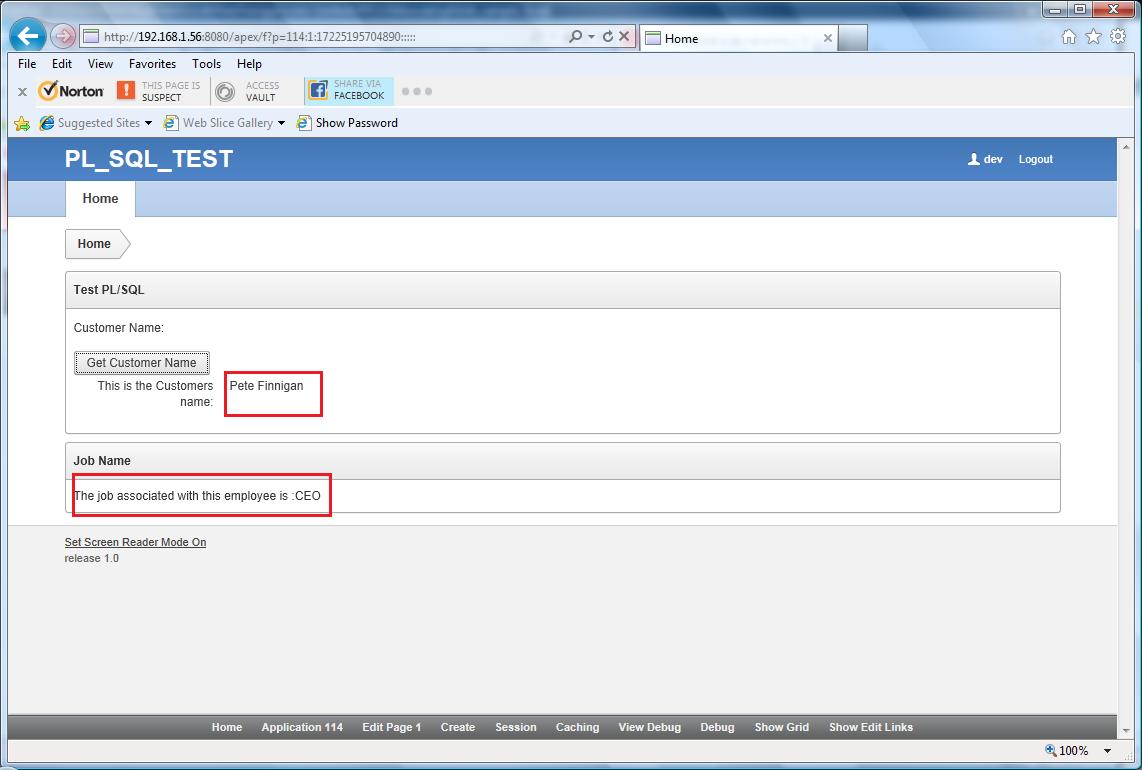
The two red boxes show where we access business logoc written in PL/SQL packages that are also deployed.
Protecting this APEX application is simple and requires a few simple steps. First set up the license.txt settings file to allow the application to work and to be licensed for 30 days:
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>type license.txt
expire_days=30
expire_date=15-AUG-2015
start_date=15-JUL-2015
license_type=trial
Now we must remove the existing PL/SQL from the database as we are going to replace it with obfuscated and protected PL/SQL where the identifiers will change. There is no point to leave the original clear PL/SQL in the database and install a protected version along side. This removal is not shown here to save space and is not critical to the understanding of this protection process. Next export the APEX application. I did this from the APEX UI and this is simple and a file f114.sql is saved to my desktop.
Now we must obfuscate the PL/SQL that is part of the application. This is simple and we use shipped configurations and policies that come with PFCLObfuscate. I had to make no configuration changes at all but Your Mileage May Vary depending on whether your PL/SQL interfaces also need to be used via other PL/SQL code or other interfaces; if so you may also need to specifiy which interfaces should be omitted from the obfuscation process. Here is the obfuscation of my applications PL/SQL:
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>obs -v -c ob_l.conf -i obs_p.sql -o obs_p.opf
PFCLObfuscate: Release 2.0.412.1254 - Production on Tue Jul 21 12:53:09 2015
Copyright (c) 2015 PeteFinnigan.com Limited. All rights reserved.
[2015 Jul 21 11:53:09] obs: Starting PFCLObfuscate...
[2015 Jul 21 11:53:09] obs: Pre-Load Keywords from [key.txt]
[2015 Jul 21 11:53:09] obs: Pre-Load Omit words from [omit.txt]
[2015 Jul 21 11:53:09] obs: Pre-Load StringOmit words from [string.txt]
[2015 Jul 21 11:53:09] obs: Pre-Load Reserved words from [reserved.txt]
[2015 Jul 21 11:53:09] obs: Pre-Load force words from [force.txt]
[2015 Jul 21 11:53:09] obs: Pre-Load function file list from [functionfile.txt]
[2015 Jul 21 11:53:09] obs: Pre-Load map file list from [map.txt]
[2015 Jul 21 11:53:09] obs: Initialise the string file list...
[2015 Jul 21 11:53:09] obs: Version 2.0 Initialisation...
[2015 Jul 21 11:53:09] obs: Initialise the file list...
[2015 Jul 21 11:53:09] obs: Initialise the Depth Stack...
[2015 Jul 21 11:53:09] obs: Initialise the FWD Function list...
[2015 Jul 21 11:53:09] obs: Initialise the FUNC function list...
[2015 Jul 21 11:53:09] obs: Initialise the NEW function list...
[2015 Jul 21 11:53:09] obs: Running PFCLObfuscate PL/SQL Obfuscator
[2015 Jul 21 11:53:09] obs: Obfuscating PL/SQL Input File [ obs_p.sql ]
[2015 Jul 21 11:53:09] obs: Save the transposed variables
[2015 Jul 21 11:53:09] obs: Process intermediate file...
[2015 Jul 21 11:53:09] obs: Closing Down PFCLObfuscate
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>obs -v -c ob.conf -i pfclob_sample_h.sql -o pfclob_sample_h.opf
PFCLObfuscate: Release 2.0.412.1254 - Production on Tue Jul 21 12:53:35 2015
Copyright (c) 2015 PeteFinnigan.com Limited. All rights reserved.
[2015 Jul 21 11:53:35] obs: Starting PFCLObfuscate...
[2015 Jul 21 11:53:35] obs: Pre-Load Keywords from [key.txt]
[2015 Jul 21 11:53:35] obs: Pre-Load Omit words from [omit.txt]
[2015 Jul 21 11:53:35] obs: Pre-Load StringOmit words from [string.txt]
[2015 Jul 21 11:53:35] obs: Pre-Load Reserved words from [reserved.txt]
[2015 Jul 21 11:53:35] obs: Pre-Load force words from [force.txt]
[2015 Jul 21 11:53:35] obs: Pre-Load function file list from [(null)]
[2015 Jul 21 11:53:35] obs: Pre-Load map file list from [map.txt]
[2015 Jul 21 11:53:35] obs: Initialise the string file list...
[2015 Jul 21 11:53:35] obs: Version 2.0 Initialisation...
[2015 Jul 21 11:53:35] obs: Initialise the file list...
[2015 Jul 21 11:53:35] obs: Initialise the Depth Stack...
[2015 Jul 21 11:53:35] obs: Initialise the FWD Function list...
[2015 Jul 21 11:53:35] obs: Initialise the FUNC function list...
[2015 Jul 21 11:53:35] obs: Initialise the NEW function list...
[2015 Jul 21 11:53:35] obs: Running PFCLObfuscate PL/SQL Obfuscator
[2015 Jul 21 11:53:35] obs: Obfuscating PL/SQL Input File [ pfclob_sample_h.sql ]
[2015 Jul 21 11:53:35] obs: Save the transposed variables
[2015 Jul 21 11:53:35] obs: Closing Down PFCLObfuscate
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>obs -v -c ob.conf -i pfclob_sample_b.sql -o pfclob_sample_b.opf
PFCLObfuscate: Release 2.0.412.1254 - Production on Tue Jul 21 12:53:53 2015
Copyright (c) 2015 PeteFinnigan.com Limited. All rights reserved.
[2015 Jul 21 11:53:53] obs: Starting PFCLObfuscate...
[2015 Jul 21 11:53:53] obs: Pre-Load Keywords from [key.txt]
[2015 Jul 21 11:53:53] obs: Pre-Load Omit words from [omit.txt]
[2015 Jul 21 11:53:53] obs: Pre-Load StringOmit words from [string.txt]
[2015 Jul 21 11:53:53] obs: Pre-Load Reserved words from [reserved.txt]
[2015 Jul 21 11:53:53] obs: Pre-Load force words from [force.txt]
[2015 Jul 21 11:53:53] obs: Pre-Load function file list from [(null)]
[2015 Jul 21 11:53:53] obs: Pre-Load map file list from [map.txt]
[2015 Jul 21 11:53:53] obs: Initialise the string file list...
[2015 Jul 21 11:53:53] obs: Version 2.0 Initialisation...
[2015 Jul 21 11:53:53] obs: Initialise the file list...
[2015 Jul 21 11:53:53] obs: Initialise the Depth Stack...
[2015 Jul 21 11:53:53] obs: Initialise the FWD Function list...
[2015 Jul 21 11:53:53] obs: Initialise the FUNC function list...
[2015 Jul 21 11:53:53] obs: Initialise the NEW function list...
[2015 Jul 21 11:53:53] obs: Running PFCLObfuscate PL/SQL Obfuscator
[2015 Jul 21 11:53:53] obs: Obfuscating PL/SQL Input File [ pfclob_sample_b.sql ]
[2015 Jul 21 11:53:53] obs: Save the transposed variables
[2015 Jul 21 11:53:53] obs: Closing Down PFCLObfuscate
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>
Next I needed to re-install this now protected supporting PL/SQL logic into my database:
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>sqlplus /nolog
SQL*Plus: Release 11.1.0.7.0 - Production on Tue Jul 21 12:54:53 2015
Copyright (c) 1982, 2008, Oracle. All rights reserved.
SQL> connect pfclob/pfclob@//192.168.1.56:1521/xe
Connected.
SQL> @obs_p.opf
Procedure created.
SQL> @pfclob_sample_h.opf
Package created.
SQL> @pfclob_sample_b.opf
Package body created.
SQL>
Finally I need to obfuscate the f{nnn}.sql APEX application export file. This is done simply:
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>obs -v -c ob_a.conf -i f114.sql -o f114.opf
PFCLObfuscate: Release 2.0.412.1254 - Production on Tue Jul 21 12:56:45 2015
Copyright (c) 2015 PeteFinnigan.com Limited. All rights reserved.
[2015 Jul 21 11:56:45] obs: Starting PFCLObfuscate...
[2015 Jul 21 11:56:45] obs: Pre-Load Keywords from [key.txt]
[2015 Jul 21 11:56:45] obs: Pre-Load Omit words from [omit.txt]
[2015 Jul 21 11:56:45] obs: Pre-Load StringOmit words from [string.txt]
[2015 Jul 21 11:56:45] obs: Pre-Load Reserved words from [reserved.txt]
[2015 Jul 21 11:56:45] obs: Pre-Load force words from [force.txt]
[2015 Jul 21 11:56:45] obs: Pre-Load function file list from [functionfile_apex.txt]
[2015 Jul 21 11:56:45] obs: Pre-Load map file list from [map.txt]
[2015 Jul 21 11:56:45] obs: Initialise the string file list...
[2015 Jul 21 11:56:45] obs: Version 2.0 Initialisation...
[2015 Jul 21 11:56:45] obs: Initialise the file list...
[2015 Jul 21 11:56:45] obs: Initialise the Depth Stack...
[2015 Jul 21 11:56:45] obs: Initialise the FWD Function list...
[2015 Jul 21 11:56:45] obs: Initialise the FUNC function list...
[2015 Jul 21 11:56:45] obs: Initialise the NEW function list...
[2015 Jul 21 11:56:45] obs: Running PFCLObfuscate PL/SQL Obfuscator
[2015 Jul 21 11:56:45] obs: Obfuscating PL/SQL Input File [ f114.sql ]
[2015 Jul 21 11:56:46] obs: Save the transposed variables
[2015 Jul 21 11:56:46] obs: Closing Down PFCLObfuscate
I can now install the APEX application back into the database - I used SQL*Plus but I could also import via the APEX UI - Both are fine. Here is the install (import):
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>sqlplus /nolog
SQL*Plus: Release 11.1.0.7.0 - Production on Tue Jul 21 12:57:08 2015
Copyright (c) 1982, 2008, Oracle. All rights reserved.
SQL> connect pfclob/pfclob@//192.168.1.56:1521/xe
Connected.
SQL> @f114.opf
APPLICATION 114 - PL_SQL_TEST
Set Credentials...
Check Compatibility...
Set Application ID...
...ui types
...user interfaces
...plug-in settings
...authorization schemes
...navigation bar entries
...application processes
...application items
...application level computations
...Application Tabs
...Application Parent Tabs
...Shared Lists of values
...Application Trees
...page groups
...comments: requires application express 2.2 or higher
...PAGE 1: Home
...PAGE 101: Login
...lists
...breadcrumbs
...page templates for application: 114
......Page template 2444509838750589
......Page template 2444720058750591
......Page template 2445321588750592
......Page template 2446015795750592
......Page template 2446521648750592
......Page template 2447126178750592
......Page template 2448016511750593
......Page template 2448814831750593
......Page template 2449707396750593
......Page template 2450426942750594
......Page template 2451200886750594
......Page template 2452020192750594
......Page template 2452206544750594
......Page template 2452708960750595
......Page template 2453518835750595
......Page template 2454425259750595
......Page template 2455108378750596
...button templates
......Button Template 2461305145750605
......Button Template 2461429858750605
......Button Template 2461526415750605
......Button Template 2461623966750605
......Button Template 2461709378750605
......Button Template 2461828655750605
...region templates
......region template 2455904650750596
......region template 2456031894750598
......region template 2456102194750598
......region template 2456219643750598
......region template 2456331358750599
......region template 2456413590750599
......region template 2456507428750599
......region template 2456614037750599
......region template 2456706521750599
......region template 2456916249750599
......region template 2457001076750599
......region template 2457110951750599
......region template 2457221859750599
......region template 2457429853750599
......region template 2457521360750599
......region template 2457609558750600
......region template 2457915937750600
......region template 2458013206750600
...List Templates
......list template 2459225586750602
......list template 2459318717750603
......list template 2459412831750603
......list template 2459503553750603
......list template 2459616117750603
......list template 2459725191750603
......list template 2459821337750603
......list template 2459927817750603
......list template 2460021392750603
......list template 2460115486750603
......list template 2460224935750603
......list template 2460320173750603
......list template 2460430663750604
......list template 2460527214750604
...report templates
......report template 2458124779750600
......report template 2458228510750601
......report template 2458313434750601
......report template 2458421120750601
......report template 2458508972750601
......report template 2458603257750601
......report template 2458732441750601
......report template 2458827252750602
......report template 2458903732750602
......report template 2459021463750602
......report template 2459106695750602
...label templates
......label template 2460616201750604
......label template 2460720568750604
......label template 2460801712750604
......label template 2460912394750604
......label template 2461023377750604
......label template 2461124440750604
......label template 2461201226750604
...breadcrumb templates
......template 2461908766750605
...popup list of values templates
......template 2462127354750607
...calendar templates
......template 2462030356750606
...application themes
......theme 2462206002750612
...theme styles
...theme display points
...build options
...Language Maps for Application 114
...text messages
...dynamic translations
...Shortcuts
...web services (9iR2 or better)
...shared queries
...report layouts
...authentication schemes
......authentication 2462510987750625
...ui types
...plugins
...data loading
...post import process
...done
SQL>
Now I can attempt to use the application and see if it works:
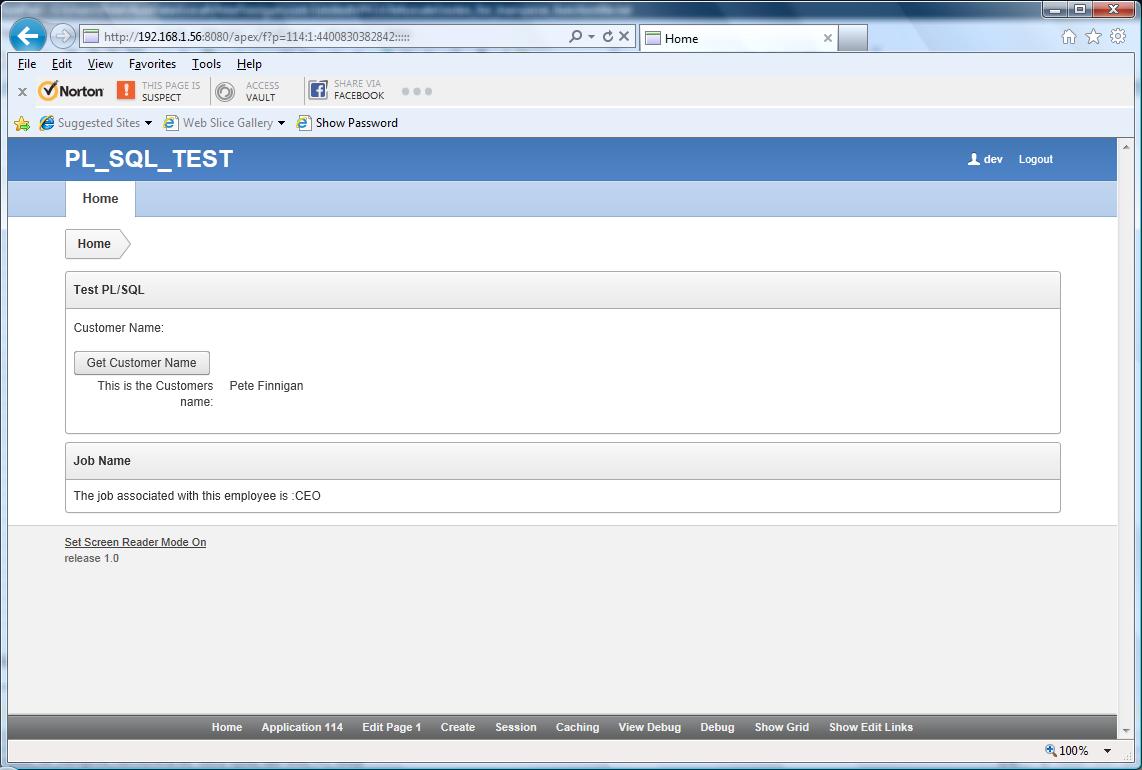
Everything in the simple application works fine still BUT its enabled for use for 30 days and also the code is obfuscated. So let's prove that by editing the license so that it has expired already; re-protecting PL/SQL and re-installing:
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>type license.txt
expire_days=30
expire_date=15-JUL-2015
start_date=15-JUN-2015
license_type=trial
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>
-- re-obfuscate
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>obs -v -c ob_l.conf -i obs_p.sql -o obs_p.opf
PFCLObfuscate: Release 2.0.412.1254 - Production on Tue Jul 21 13:01:19 2015
Copyright (c) 2015 PeteFinnigan.com Limited. All rights reserved.
[2015 Jul 21 12:01:19] obs: Starting PFCLObfuscate...
[2015 Jul 21 12:01:19] obs: Pre-Load Keywords from [key.txt]
[2015 Jul 21 12:01:19] obs: Pre-Load Omit words from [omit.txt]
[2015 Jul 21 12:01:19] obs: Pre-Load StringOmit words from [string.txt]
[2015 Jul 21 12:01:19] obs: Pre-Load Reserved words from [reserved.txt]
[2015 Jul 21 12:01:19] obs: Pre-Load force words from [force.txt]
[2015 Jul 21 12:01:19] obs: Pre-Load function file list from [functionfile.txt]
[2015 Jul 21 12:01:19] obs: Pre-Load map file list from [map.txt]
[2015 Jul 21 12:01:19] obs: Initialise the string file list...
[2015 Jul 21 12:01:19] obs: Version 2.0 Initialisation...
[2015 Jul 21 12:01:19] obs: Initialise the file list...
[2015 Jul 21 12:01:19] obs: Initialise the Depth Stack...
[2015 Jul 21 12:01:19] obs: Initialise the FWD Function list...
[2015 Jul 21 12:01:19] obs: Initialise the FUNC function list...
[2015 Jul 21 12:01:19] obs: Initialise the NEW function list...
[2015 Jul 21 12:01:19] obs: Running PFCLObfuscate PL/SQL Obfuscator
[2015 Jul 21 12:01:19] obs: Obfuscating PL/SQL Input File [ obs_p.sql ]
[2015 Jul 21 12:01:19] obs: Save the transposed variables
[2015 Jul 21 12:01:19] obs: Process intermediate file...
[2015 Jul 21 12:01:19] obs: Closing Down PFCLObfuscate
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>
-- re-isnatll to the database
C:\Users\Pete\AppData\Local\PeteFinnigan.com Limited\PFCLObfuscate>sqlplus /nolog
SQL*Plus: Release 11.1.0.7.0 - Production on Tue Jul 21 13:02:39 2015
Copyright (c) 1982, 2008, Oracle. All rights reserved.
SQL> connect pfclob/pfclob@//192.168.1.56:1521/xe
Connected.
SQL> @obs_p.opf
Procedure created.
SQL>
Now if I run the application again the login fails with a license exception:
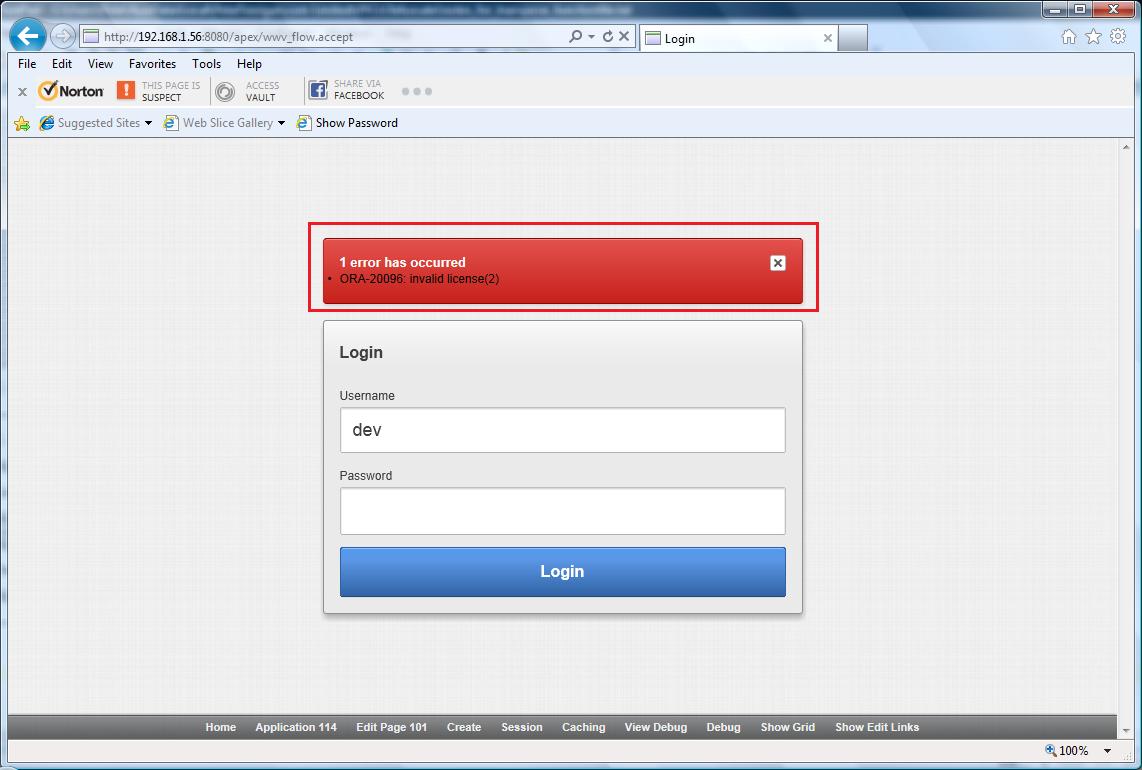
The red box shows the license exception thrown by the protection. The advantage of PFCLObfuscate is that you can worry about the protection after the development is complete and apply it automatically to your code (supporting PL/SQL and also the application export file - the f{nnn}.sql file)
So thats it; if you would like more details about our product PFCLObfuscate or to buy a license then please email me at "pete at petefinnigan dot com". Thanks for listening!